C4H - Ransomware

Static Analysis
SHA256: C317B7E34197C707D9C7D642B259A6798763A53C81E226F197661F62AF41A82A
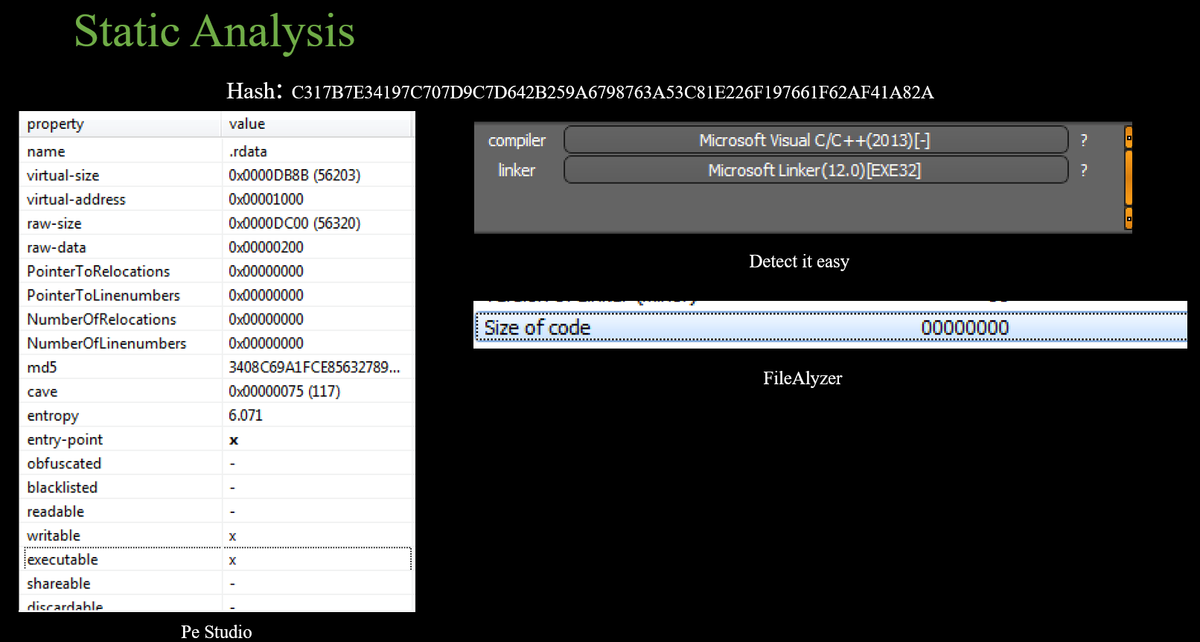
The sample is a 32-bit executable with an unusual structure, as it contains only one section, unlike standard PE files, which typically have multiple sections. The .rdata section is both executable and writable, an uncommon combination that strongly suggests the file is packed, with the actual code likely being extracted at runtime. Additionally, the file is marked with a code size of 0, further supporting this indication.
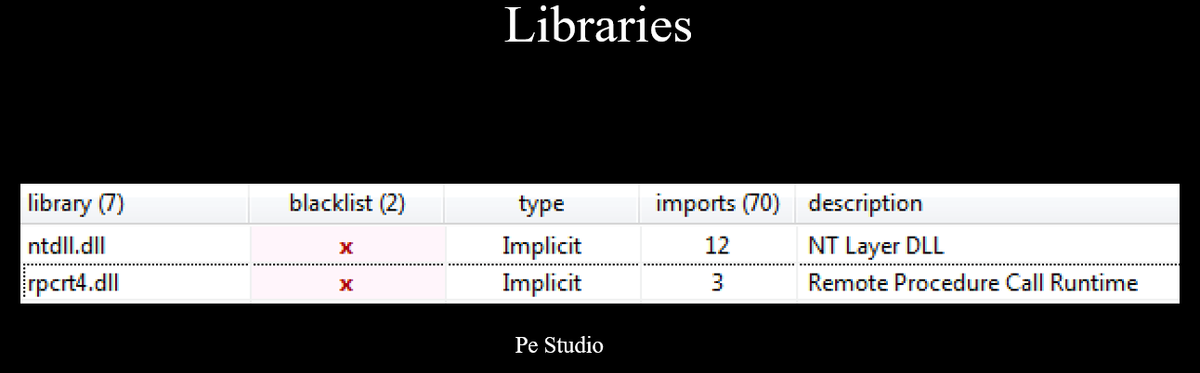
After examining the file in PE Studio, it is evident that it relies heavily on two main libraries: ntdll.dll, which provides kernel-level functions, and rpcrt4.dll, which is primarily used by applications for network-related capabilities.
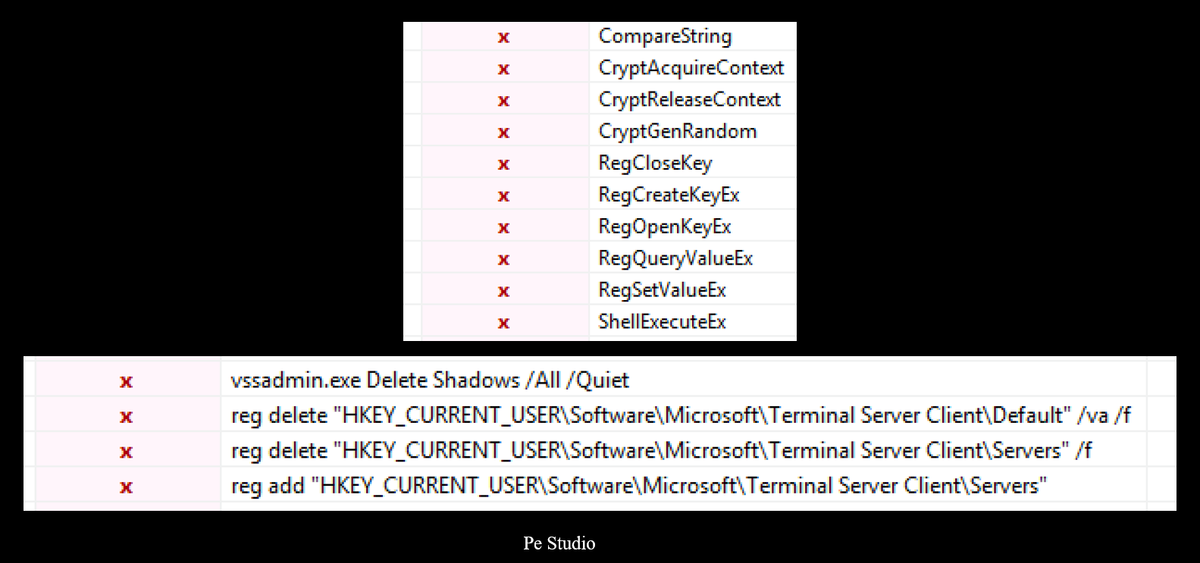
By analyzing the strings in PE Studio, I found that the file utilizes multiple cryptographic and registry functions, as well as Windows shell commands. The file modifies Terminal Server registry keys by adding and deleting entries. Additionally, it executes the command:
vssadmin.exe Delete Shadows /All /Quiet
This command is used to delete all shadow copies on the machine silently, without prompting the user. Shadow copies are snapshots of files or volumes that allow for recovery in case of accidental changes or ransomware attacks. By deleting these copies, the malware ensures that victims cannot restore their files using backup snapshots, increasing the pressure to pay the ransom.
Dynamic Analysis
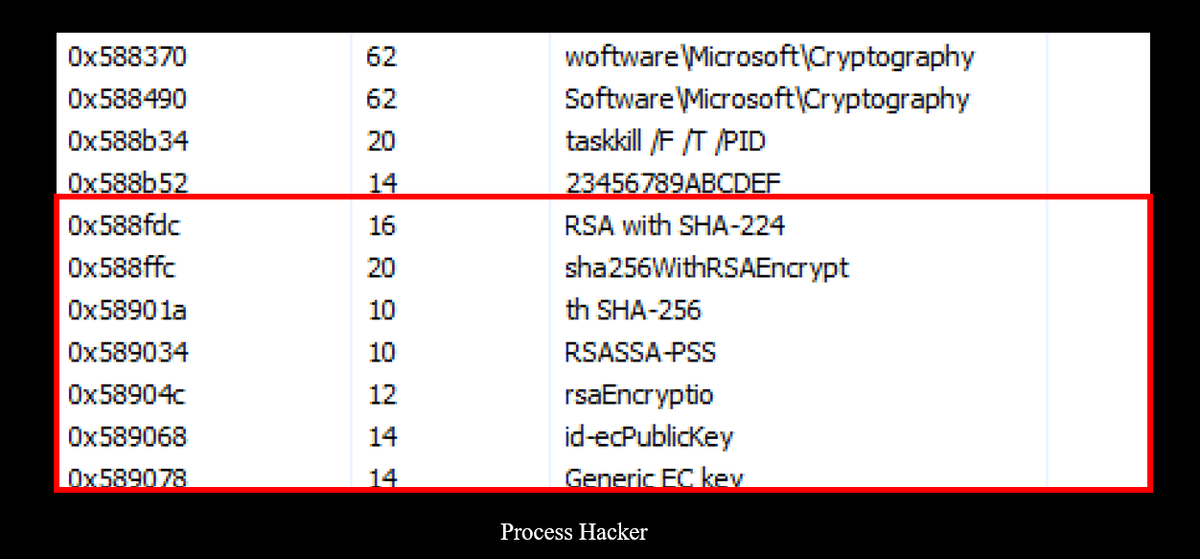
During my dynamic analysis, after executing the file and monitoring the memory strings using Process Hacker, I identified additional string attributes related to the encryption algorithm. Notably, I observed references to encryption keys and the RSA algorithm, specifically RSA with SHA-224, indicating its use for securing data and key exchange during the encryption process.
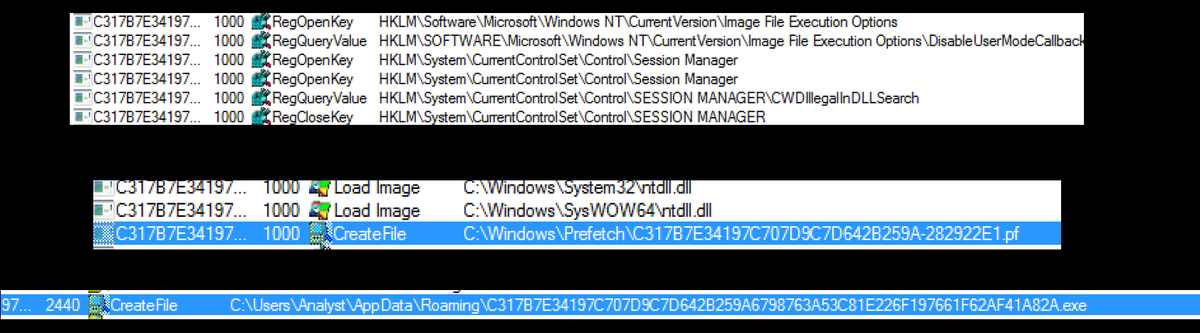
Monitoring the file using Procmon reveals that it opens and queries several registry keys, including the CWDIllegalInDllSearch key at HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager. This key controls the DLL search order and determines whether DLLs can be loaded from the current working directory (CWD), helping prevent DLL hijacking.
The file also accesses the HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager path, indicating reconnaissance activity to gather system details and assess vulnerabilities, such as unsafe DLL loading configurations.
The malware creates a password-protected and encrypted .pf file in the Prefetch folder located at C:\Windows\Prefetch\
The malware drops a copy of itself in the C:\Users\User\AppData\Roaming folder to maintain persistence.
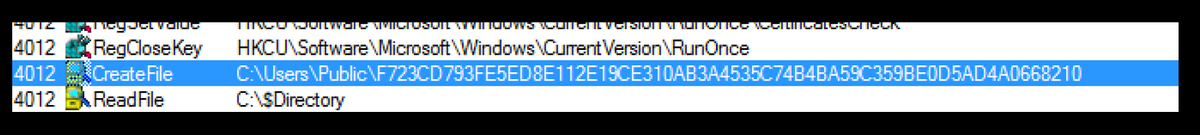
It creates another file, this time in the Users\Public folder, designed to internally store user information.
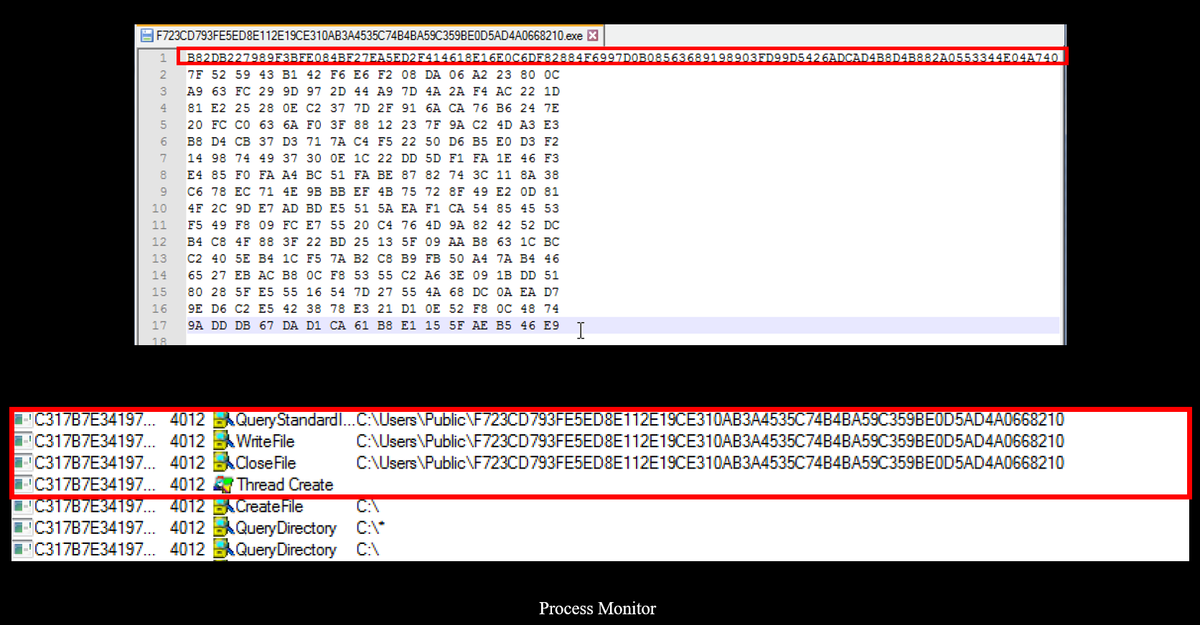
The file contains the user's personal ID, which is displayed in the ransom note within the HTML file. It is assumed that the first line of the file is related to the encryption key, as the file is queried and modified immediately before the encryption thread is created.
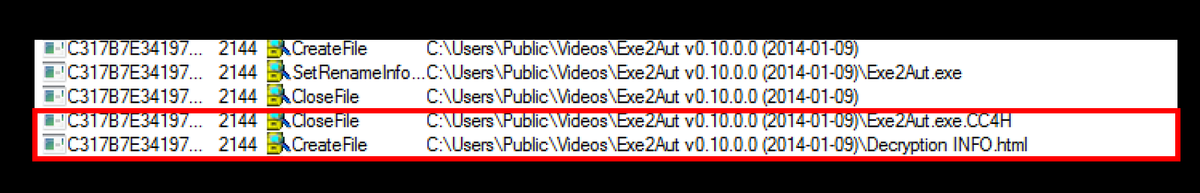
After the encryption thread starts, files are rewritten with the .CC4H extension, and a Decryption INFO.html ransom note file is created in the directory containing those files.
The malware belongs to the GlobeImposter ransomware family, distributed via spam emails and fake ads. It uses a hybrid AES-RSA encryption algorithm, offering strong security and efficient data transmission.