Ave Maria Infostealer

Static Analysis
SHA256: 653E5E8F8259270524173DD4D52C280755E69E959B1293F0FAE29C7CAA2E2C3
On a first encounter you can see that the file is a C++ 32 bit executable, it has 4 sections, no suspicious sections privileges with the .text section being the entry point and only readable and executable section.
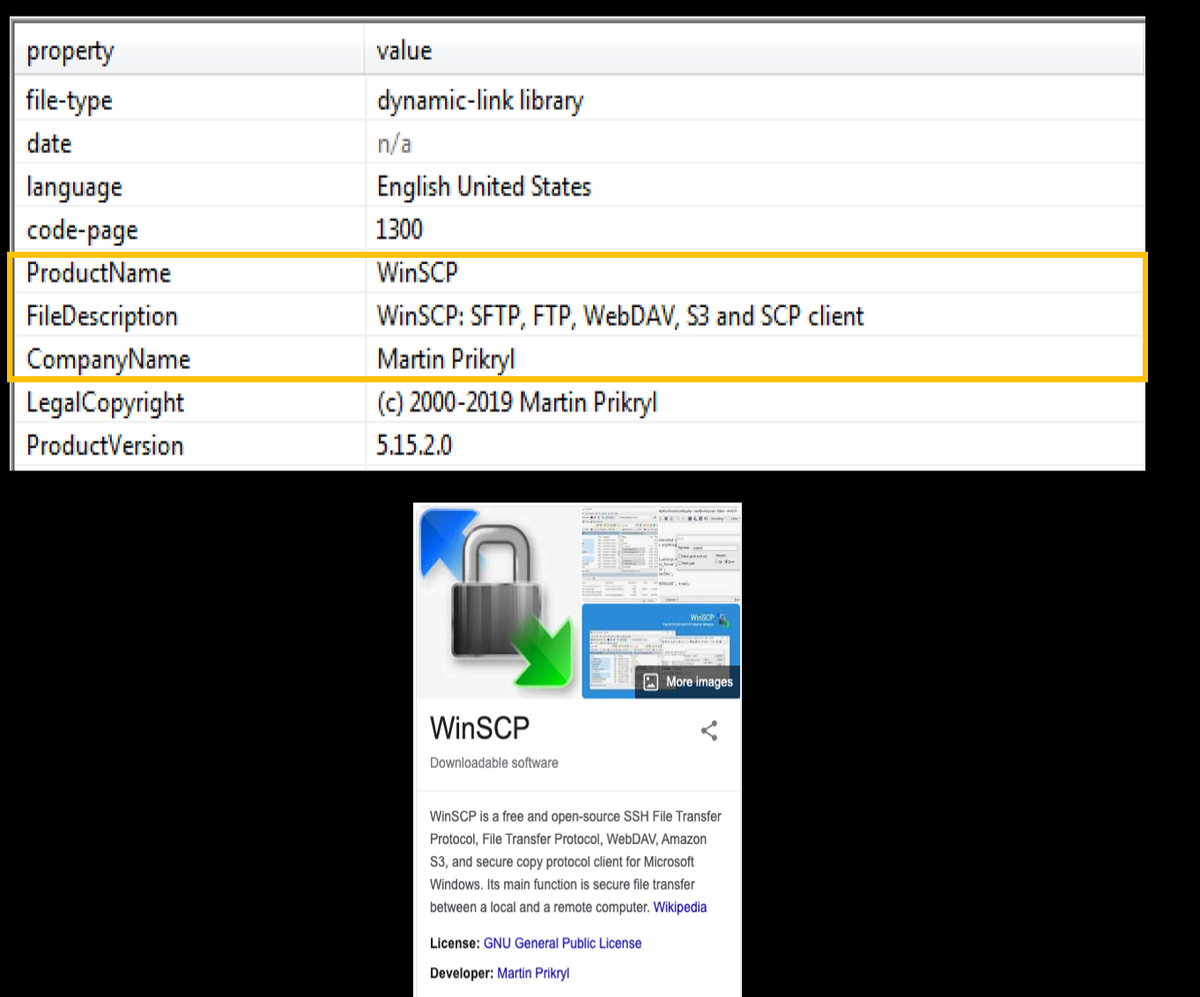
Now looking on the version information on PE Studio, you can see that the file pretends to be this WINSCP application which is a legitimate open source software for secure file transfer between a local and a remote machine.
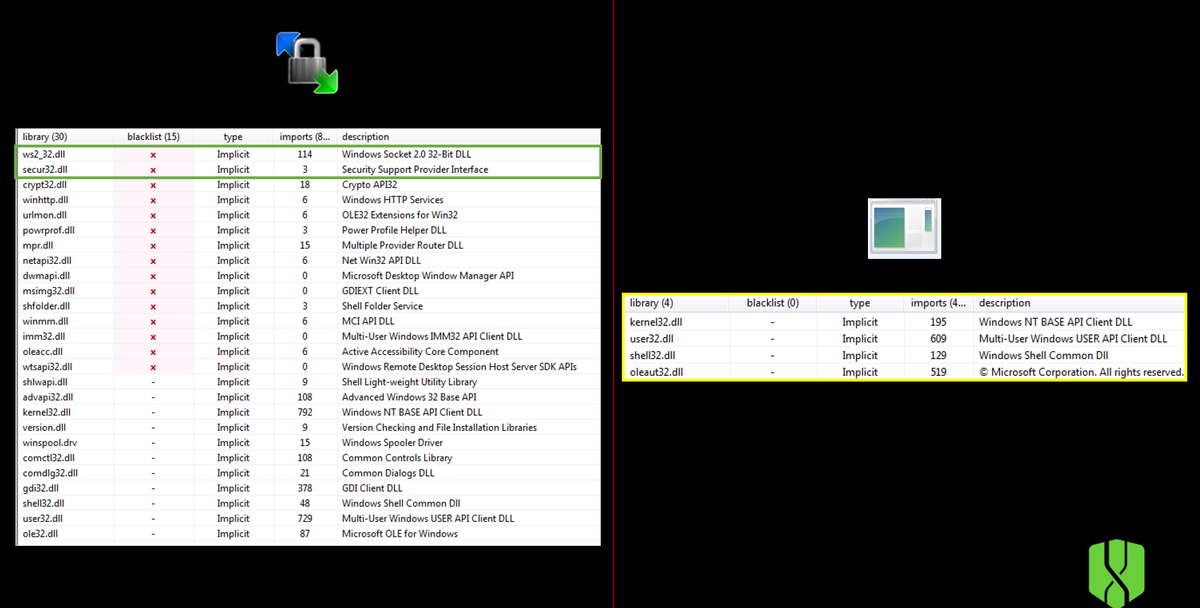
I was certain that this wasn’t a legitimate software. but out of curiosity I downloaded the official WINSCP software mainly to have a look at the libraries imports being used and compare to my file. My sample was only using 4 libraries imports. The kernel, userAPI, The Shell and the Object Linking Automation. While the official software was using many as expected. The key difference being that the official file actually uses the Windows Socket and Security Support Provider libraries which I would say are the main imports you need for a software that provides a file transfer service.
Looking at the strings on PE Studio, these were the most telling API functions. Straight away you can see the ShellExecuteEx and GetCommandLine functions being referenced.

Also the VirtualProtect function which enables to change the permissions on a page in memory. Also the reference to the IsDebuggerPresent function which allows the file to check if It’s being debugged or not, so it can potentially change it’s behaviour on the go.

Dynamic Analysis
Upon executing and monitoring the file in Process Monitor, you can see the launch of the Command Prompt and PowerShell processes, as expected based on the static analysis.
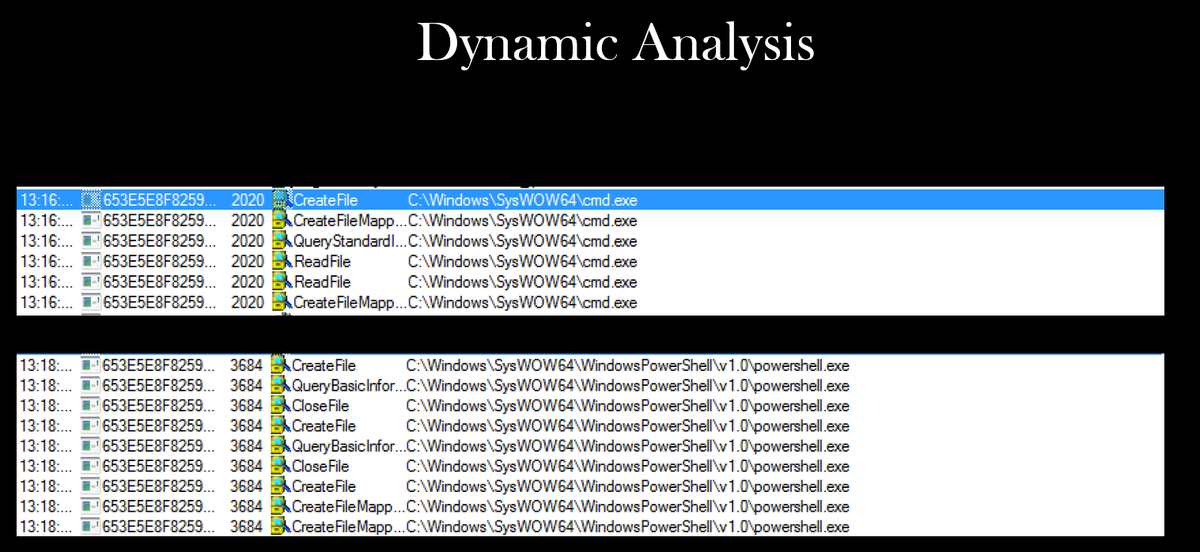
The sample drops this image executable process inside the AppData\Roaming folder.
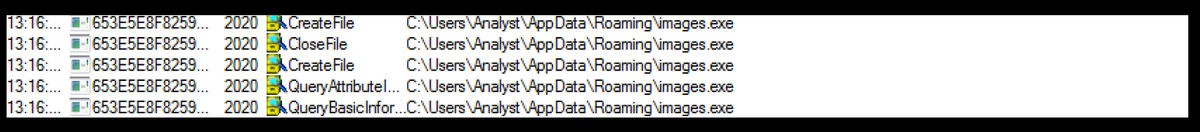
Here is the process tree for both files. As you can see, both files use the same process, indicating that one is a copy of the other. It has copied itself to the AppData\Roaming folder.
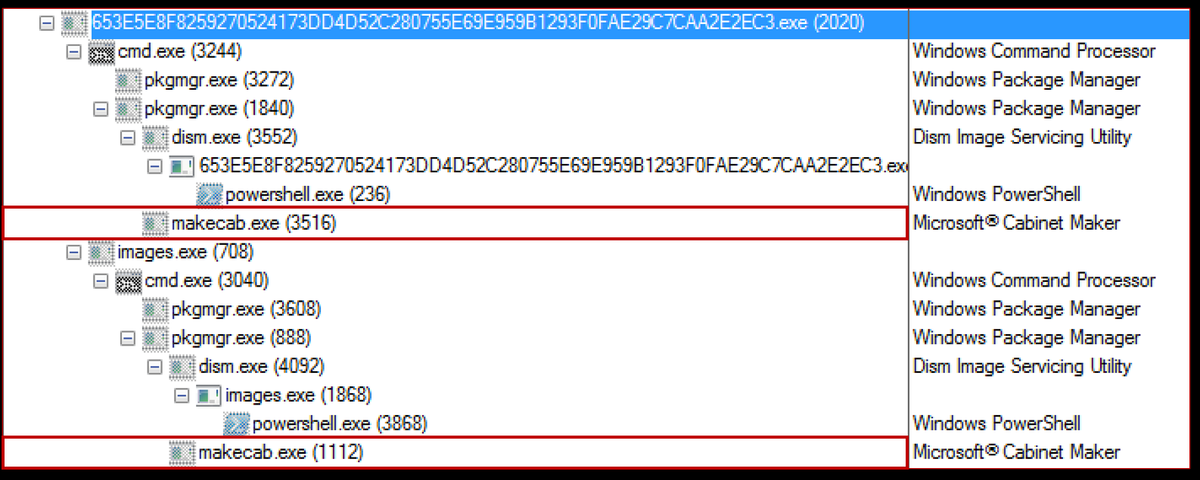
After a few seconds of the file being executed this window was launched, I researched about this Loss Data Compression tool process and found relation to this CAB file that was opened it allows components to communicate with each other; it contains computer-level attributes; And it also stores information across programs within the computer. But to be honest up to this point I didn’t know what to make of all this. I didn't have a clear picture on what the malware was trying to do ...
I examined the strings in memory of the dropped image's process. As you can see, there are references to Firefox browser profile logins, including encrypted usernames and passwords. Additionally, the process contains a reference to Thunderbird, an email client developed by Mozilla.
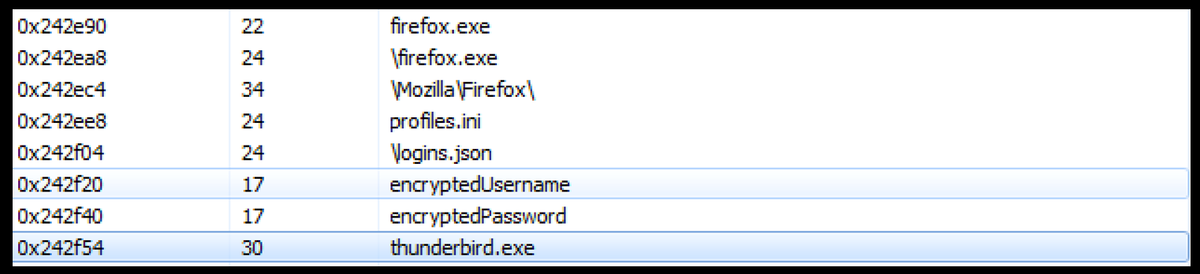
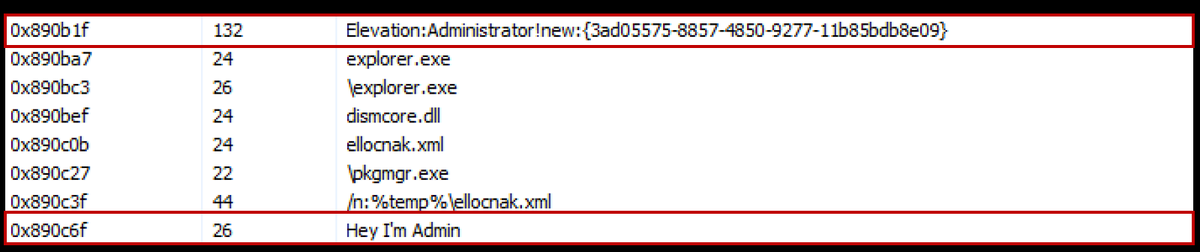
There is also a nice elevation privilege reference.
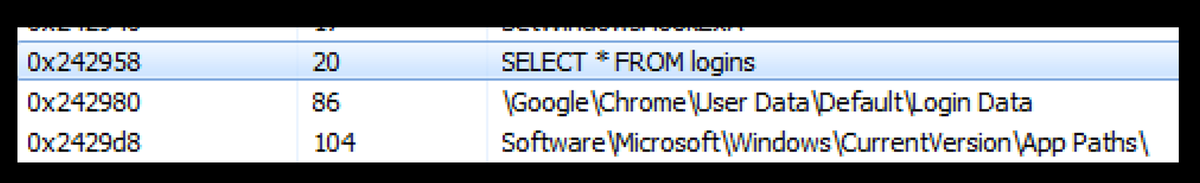
Here is a reference to a database query, followed by a reference to Google Chrome's Login Data, indicating a breach of browser data.
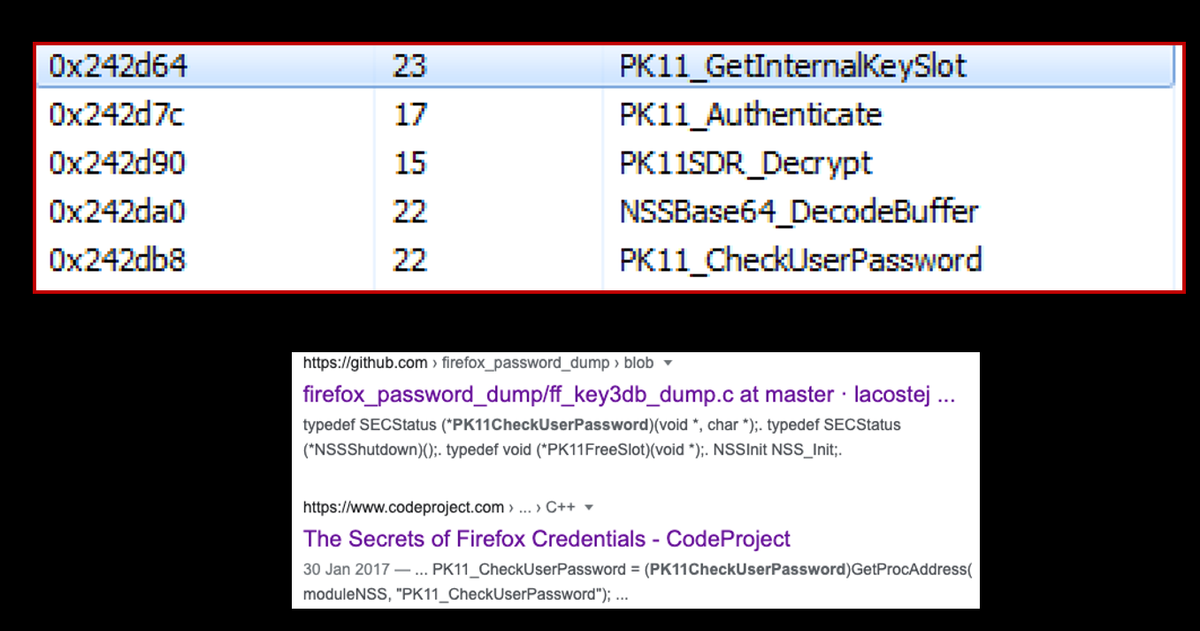
Doing a bit of OSINT, I found that all of these PK11 references are functions from the Firefox browser that are typically used to decrypt and crack browser login passwords.
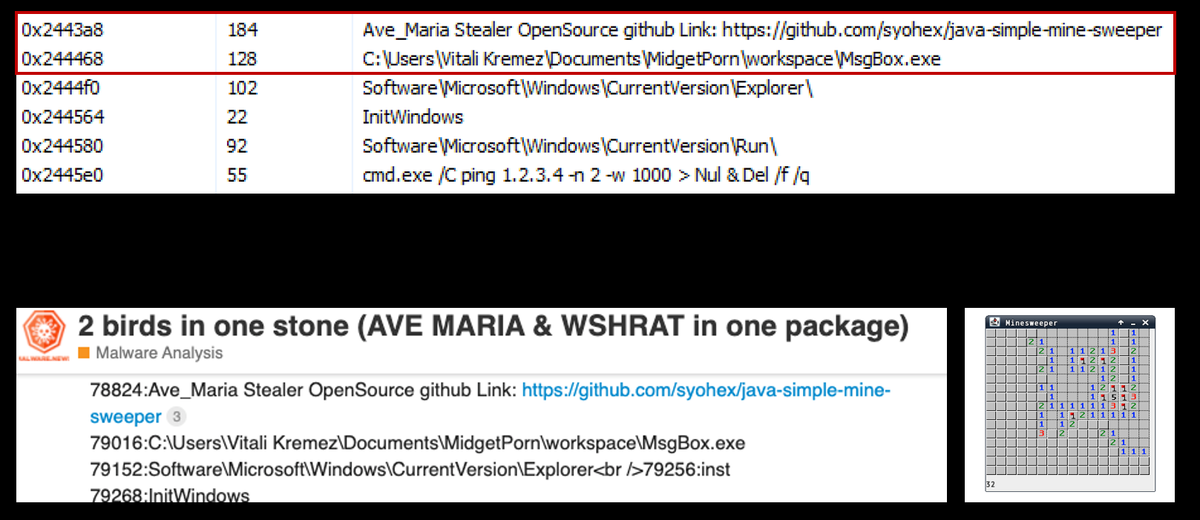
The Ave Maria Stealer and the associated path were the most compelling references I found in memory. After researching these references, I discovered that they are linked to AveMaria, a RAT malware. Additionally, there is a reference to the Software\Microsoft\Windows\CurrentVersion\Run registry path, which indicates persistence, as the process will automatically start when the user logs in.
The malware also executes the following command:cmd.exe /C ping 1.2.3.4 -n 2 -w 1000 > Nul & Del /f /q
The command checks network connectivity by pinging a remote IP, discards the output to avoid detection, and then quietly deletes a file, to clean up malicious components and avoid leaving traces.
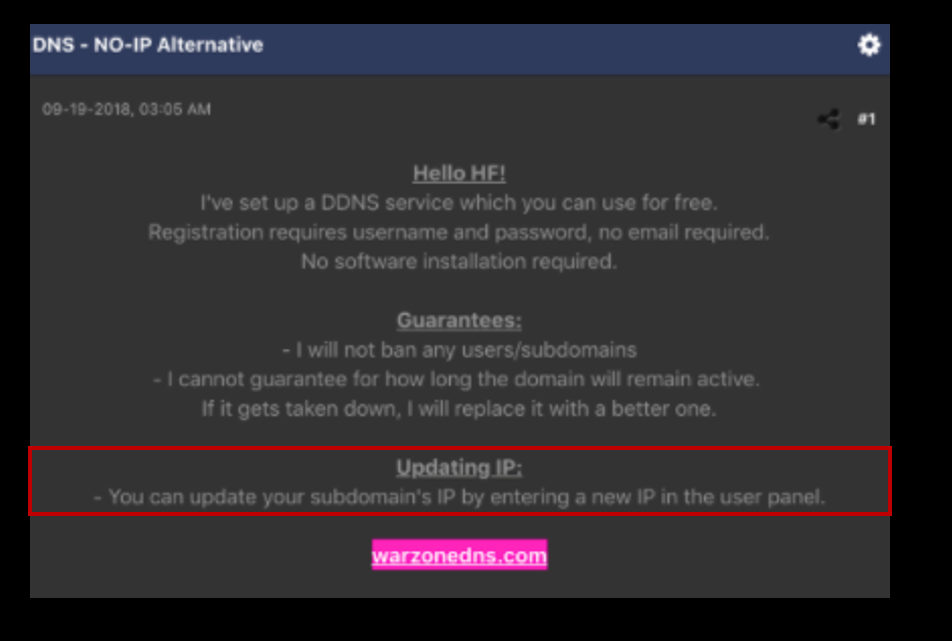
Throughout the strings in memory, I found numerous references to this warzonedns URL.

While researching the warzonedns domain, I discovered that it is a free Dynamic DNS service, commonly used by malware authors. This service allows for quick changes to subdomain IP addresses, making it a popular choice for malicious activities. The last time I checked, however, the domain was no longer available.